
Photo by KeepCoding on Unsplash
Cyber Security 101: Introduction to Cyber Security
Everything you need to know to get started in Cyber Security
Cybersecurity refers to any technology, measures or practices that help protect computer systems, networks, programs and data from cyber attacks like malware, phishing and ransomware.
Some fundamentals of cybersecurity include:
Confidentiality
This refers to measures taken to keep data secret and private. It involves protecting data like credit card info, SSN, passwords, healthcare records, etc. from unauthorized access. Phishing and man-in-the-middle attacks threaten confidentiality.
Integrity
This ensures data remains accurate and unchanged. It involves using encryption, access controls, auditing, etc. Compromised integrity can lead to data manipulation and theft.
Availability
This ensures systems, networks and data are accessible whenever needed. It can be threatened by denial-of-service attacks and ransomware. Redundancy and backups help with availability.
Some basic cybersecurity terminologies are:
IP address: Unique identifier for devices on a network
VPN: Encrypted network connection
Firewall: Network security system that filters traffic
DNS: Converts domain names to IP addresses
Encryption: Encoding data to prevent unauthorized access
Threats in Cyber Security
What are Cybersecurity Threats?
Cybersecurity threats are acts performed by individuals with harmful intent, whose goal is to steal data, cause damage to or disrupt computing systems.
1. Social Engineering
Social engineering is the art of tricking people rather than computers to gain unauthorized access or information. Attackers exploit human psychology to deceive individuals into divulging sensitive information or performing actions that compromise security.
Imagine someone posing as a trustworthy entity—maybe a colleague, tech support, or even a friend—reaching out to you through email, phone, or social media. They might create a sense of urgency or use fear tactics to make you act quickly without thinking. Once they gain your trust, they might trick you into revealing passwords, clicking on malicious links, or downloading malware.
Humans can be the weakest link in the security chain, and that's what makes social engineering so potent. It's crucial to be skeptical and cautious, even when things seem familiar or urgent. Always verify the legitimacy of requests, especially if they involve sensitive information or actions
Check out this video about Social Engineering
2. Malware
Malware is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy.
Types of Malware
Viruses: Like a biological virus, computer viruses replicate themselves by attaching to other programs. They can damage or corrupt files and spread to other systems.
Worms: Worms are self-replicating malware that don't need a host program. They exploit network vulnerabilities to spread across computers, often slowing down networks.
Trojans: Named after the ancient Greek story of the wooden horse, Trojans disguise themselves as legitimate software but carry malicious payloads. Once inside a system, they can create backdoors for attackers.
Ransomware: This nasty type of malware encrypts a user's files and demands payment (usually in cryptocurrency) for their release. It's like digital kidnapping.
Spyware: True to its name, spyware secretly observes and collects user information. It can record keystrokes, capture screenshots, or monitor online activities without the user's knowledge.
Adware: While not as malicious as others, adware bombards users with unwanted advertisements. It can slow down systems and lead to a poor user experience.
Rootkits: These are stealthy types of malware designed to hide the presence of other malicious programs. They often have privileged access to the system, making them hard to detect.
Botnets: A botnet is a network of compromised computers, often controlled by a single entity. These "bots" can be used for various malicious activities, such as launching distributed denial-of-service (DDoS) attacks.
3. Phishing
Phishing is the practice of sending fraudulent communications that appear to come from a legitimate and reputable source, usually through email and text messaging. The attacker's goal is to steal money, gain access to sensitive data and login information, or to install malware on the victim's device.
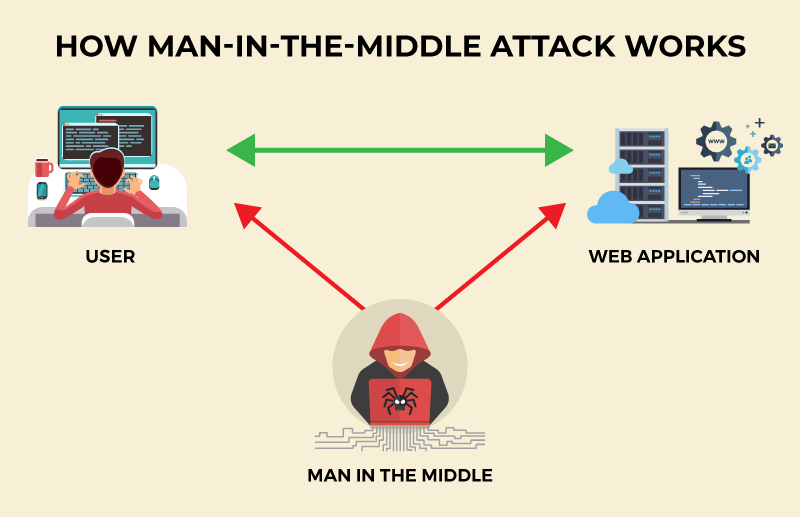
4. Man-in-the-middle attacks
A man-in-the-middle attack is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, as the attacker has inserted themselves between the two parties.
Careers in Cyber Security
Systems Administrator - also known as a sysadmin, is responsible for managing and maintaining an organization's computer systems, networks, and servers. Their primary job is to ensure that the computer infrastructure runs smoothly, securely and efficiently.
Bug Bounty Hunter - Bug bounty hunting involves identifying and reporting software bugs and vulnerabilities to companies in exchange for rewards. It allows companies to plug security holes before cybercriminals can exploit them.
The following is a guide on how to get started as a bug bounty hunter in 2023
%[youtube.com/watch?v=FDeuOhE5MhU&pp=ygUT..
Red Teamer - A Red Teamer is a cybersecurity professional who tries to identify vulnerabilities in an organization's network and systems by simulating real-world attacks. They think like a malicious hacker and attempt to exploit weaknesses to provide insight into an organization's security posture. Here are the key points about red teamers:
They adopt an adversarial perspective to identify security gaps and vulnerabilities.
Their goal is not to cause damage but to evaluate security controls and improve defenses.
They perform penetration testing, social engineering attacks, and other simulated threats.
They help organizations understand potential threats, risks, and weaknesses in their systems.
Their findings and recommendations help organizations develop stronger security strategies and incident response plans.
They possess both technical skills and creative, out-of-the-box thinking to identify unconventional vulnerabilities.
They collaborate closely with defensive security teams (blue teams) to improve security measures based on their results.
Digital Forensic Analyst - A digital forensic analyst is like a cyber detective, but in the digital realm. They investigate cybercrimes and incidents to uncover evidence and understand what happened.
Malware Analyst - A malware analyst is a cybersecurity professional who specializes in studying and analyzing malicious software, commonly known as malware. Their primary role is to dissect and understand the inner workings of different types of malware to develop effective strategies for detection, prevention, and mitigation.
Blue Teamer - A blue teamer is a cybersecurity professional who focuses on defending and securing computer systems, networks, and data from cyber threats. The term "blue team" and "red team" are often used in the context of cybersecurity exercises and practices.
Getting into Cyber Security
There are many platforms and resources to get started in cyber security
To elevate your expertise in this field, consider exploring the following recommended resources.
TryHackMe (Free) - TryHackMe is an online platform that provides hands-on cybersecurity training through virtual labs and challenges. It's designed to help individuals, whether beginners or experienced professionals, develop and enhance their practical skills in various aspects of cybersecurity
Hack The Box (Free) - Hack The Box (HTB) is an online platform that offers a hands-on and gamified approach to cybersecurity training. It provides a variety of virtual machines (VMs) that users can attempt to hack and compromise, simulating real-world scenarios.
Over The Wire (Free) - OverTheWire is a fantastic platform for individuals interested in learning and practicing cybersecurity skills. It provides a series of war games or challenges, each with its own unique set of puzzles and security scenarios.
Pico ctf (Free) - PicoCTF (Capture The Flag) is a cybersecurity competition designed for students and beginners to gain hands-on experience in various aspects of cybersecurity. It provides a platform where participants can solve a wide range of challenges related to cryptography, web exploitation, reverse engineering, binary exploitation, and more.
RootMe (Free) - RootMe is a platform that offers a collection of online challenges and virtual environments for individuals to practice and enhance their cybersecurity skills. It provides a variety of realistic scenarios, including challenges related to web security, network security, cryptography, and more.
Portswigger (Free) - PortSwigger refers to both a company and its flagship product, Burp Suite. PortSwigger is a cybersecurity company known for developing web security testing tools. Burp Suite, their most notable product, is a comprehensive platform designed for web application security testing.
CTFs (Free) - CTF stands for Capture The Flag, and in the context of cybersecurity, it refers to a type of competition or challenge where participants (often cybersecurity enthusiasts, ethical hackers, or students) attempt to solve a series of puzzles or complete specific tasks to "capture flags" and earn points. These challenges are designed to test and enhance participants' skills in various aspects of cybersecurity.
Examples of CTF challenges include:
DEF CON CTF: DEF CON is one of the largest and most well-known hacking conferences. Its Capture The Flag competition is highly competitive and features a wide range of challenges.
picoCTF: As mentioned earlier, picoCTF is an online CTF organized by Carnegie Mellon University. It's designed for students and beginners but covers a diverse set of challenges.
Hack The Box (HTB): While not a traditional CTF, Hack The Box provides a platform where users can engage in challenges to test and improve their hacking skills on a variety of realistic scenarios.
Google Capture The Flag (CTF): Google occasionally organizes online CTF events where participants can tackle challenges related to various aspects of cybersecurity.
PlaidCTF: PlaidCTF is an annual CTF competition organized by the Plaid Parliament of Pwning (PPP), a hacking team from Carnegie Mellon University. It features challenges ranging from binary exploitation to reverse engineering.
Root Me: Root Me is a platform that hosts a variety of online challenges and virtual environments for individuals to practice their cybersecurity skills.
Cyber Security Learning Resources
Here are some valuable cybersecurity learning resources across various domains:
Books / PDFs
Online Platforms:
TryHackMe: Provides hands-on cybersecurity challenges and virtual labs.
Hack The Box (HTB): Offers a platform for practicing penetration testing skills.
OverTheWire: Hosts online war games to develop and hone hacking skills.
YouTube Channels:
The Cyber Mentor: Practical cybersecurity tutorials and tips.
Hak5: Covers a variety of topics related to hacking and security.
John Hammond: Free Cybersecurity Education and Ethical Hacking.
Live Overflow: making videos about various IT security topics and participating in hacking competitions.
Tib3rius: Practice your web application security interview skills with challenging questions
Nahamsec: creates content about external attack surface management, bug bounty, smart contracts e.t.c
Hackersploit: is the leading provider of free Infosec and cybersecurity training
Capture The Flag (CTF) Platforms:
Forums and Communities:
Reddit - r/netsec: Subreddit for network security discussions.
Stack Exchange - Information Security: Q&A platform for security-related questions.
GitHub Repositories
Awesome-Hacking: A curated list of hacking tools for ethical hackers and penetration testers.
OWASP Cheat Sheet Series: Practical guides on various application security topics from the Open Web Application Security Project (OWASP).
Metasploit Framework: One of the most widely used penetration testing frameworks.
SecLists: Collection of multiple types of lists used during security assessments, including usernames, passwords, URLs, and more.
PayloadsAllTheThings: A list of useful payloads and bypasses for web application security.
Awesome-Pentest: A collection of awesome penetration testing resources.
BloodHound: An Active Directory security analysis tool.
Awesome-Web-Security: A curated list of web security resources.
Exploit Database: The official Exploit Database repository.
Hacker Roadmap: A guide for anyone interested in starting a career in cybersecurity.
Remember to practice hands-on skills, stay updated with the latest security news, and engage with the cybersecurity community for continuous learning and improvement.
Tools used in Cyber Security
Embarking on the dynamic journey of cybersecurity requires more than just theoretical knowledge—it demands a robust set of tools wielded by skilled practitioners

Operating Systems:
Two main options include: Kali Linux and Parrot Os.
- Others include:
BlackArch Linux, ArchStrike, BackBox Linux, DEFT (Digital Evidence & Forensic Toolkit), Tails (The Amnesic Incognito Live System), Qubes OS, Windows Subsystem for Linux (WSL)
- Others include:
-
Purpose: Network discovery and security auditing.
Features: Port scanning, version detection, OS fingerprinting.
-
Purpose: Network protocol analyzer.
Features: Captures and analyzes the data traveling back and forth on a network in real-time.
-
Purpose: Penetration testing and exploitation framework.
Features: Helps in developing, testing, and executing exploit code against a remote target.
-
Purpose: Web application security testing.
Features: Web vulnerability scanner, proxy, and application security tools.
-
Purpose: Intrusion Detection System (IDS).
Features: Monitors and analyzes network traffic for signs of malicious activity.
-
Purpose: Wireless network penetration testing.
Features: Mimics trusted Wi-Fi networks to intercept and manipulate network traffic.
-
Purpose: Open-source intelligence and forensics.
Features: Visualizes data relationships, helps in analyzing and mapping cyber threats.
-
Purpose: Password cracking.
Features: Supports various hashing algorithms for password recovery.
-
Purpose: Wireless network security assessment.
Features: Packet sniffer, WEP and WPA/WPA2-PSK key cracker.
-
Purpose: Windows system utilities.
Features: Collection of advanced system utilities for troubleshooting, diagnostics, and monitoring.
-
Purpose: Reverse engineering.
Features: Software reverse engineering suite developed by the NSA.
-
Purpose: Antivirus engine for detecting trojans, viruses, malware, and other malicious threats.
Features: Open-source and cross-platform.
-
Purpose: Network security monitoring.
Features: Analyzes network traffic in real-time and provides valuable insights.
-
Purpose: Memory forensics.
Features: Analyzes volatile memory dumps for signs of malicious activity.
-
Purpose: Vulnerability scanning.
Features: Open-source vulnerability scanner to identify security issues in a system.
These tools represent just a fraction of the extensive toolkit available to cybersecurity professionals. Depending on the specific task at hand, professionals may use a combination of these tools to secure systems, networks, and applications. Keep in mind that responsible and ethical use of these tools is crucial.
**
Connect with Us!**
Explore our chapter and engage with the vibrant community at the University of Eldoret through the following link:
Chapter Link: University of Eldoret GDSC
We look forward to welcoming you and fostering collaboration within our community.
Our Socials
LinkedIn - linkedin.com/company/gdsc-uoe

